There are few things worse than feeling trapped in an unfulfilling relationship – especially when it’s a vital business relationship.…


There are few things worse than feeling trapped in an unfulfilling relationship – especially when it’s a vital business relationship.…

Partnering with a Managed Service Provider can offer business owners a way to limit risks and increase productivity. Running a…

Get untangled from your landline, and let VoIP boost your business’ efficiency, reliability, and quality. A recent study revealed that…

With the growing threat of viruses, worms, scams and phishing schemes, it seems impossible for computer users to avoid a…

We all wish we had a magic crystal ball that would make our lives easier, whether that means knowing when…
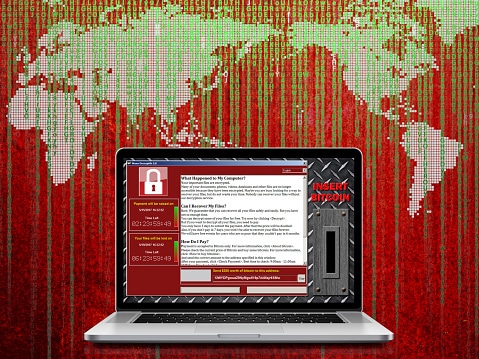
We recently came across some chilling news. A white hat hacker developed a working “Ransomcloud” strain, that encrypts cloud e-mail…

January 28th, 2018 is Data Privacy Day, an international effort led by the National Cyber Security Alliance (NCSA) annually for…

With every New Year comes the chance to reset priorities. Unfortunately, when the topic of implementing a data recovery plan…

When we consider the security of our business technology, we often think of scams or phishing e-mails. These get easily…

Do you like to dance? Dancing is both a science and an art. The waltz is a beautiful and romantic…

This is what people sometimes say when you start talking about machine language and artificial intelligence. Though it’s true that…

LinkedIn, the increasingly popular business and employment-focused social networking site is a crucial tool for professionals who are happily employed…