Earlier this year, Intel introduced their new 8th Gen Intel Core vPro processors. Marketed as the way to help businesses…


Earlier this year, Intel introduced their new 8th Gen Intel Core vPro processors. Marketed as the way to help businesses…

5 Ways to Reclaim Your Time There are hardly any jobs in the modern world that permit you to work…

Windows 7 Is Being Sunset Within The Next 2 Years (Questions & Answers) Microsoft announced they are stopping mainstream support…

In today’s business world, it’s important for companies to stay ahead of the trends when it comes to the latest…
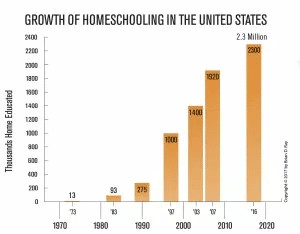
Independent schools have a prime opportunity to increase enrollment right now. Trust in government agencies is mixed to low, and…

Vacation and time away from work is a necessity in order to be able to unplug and recharge. As research…
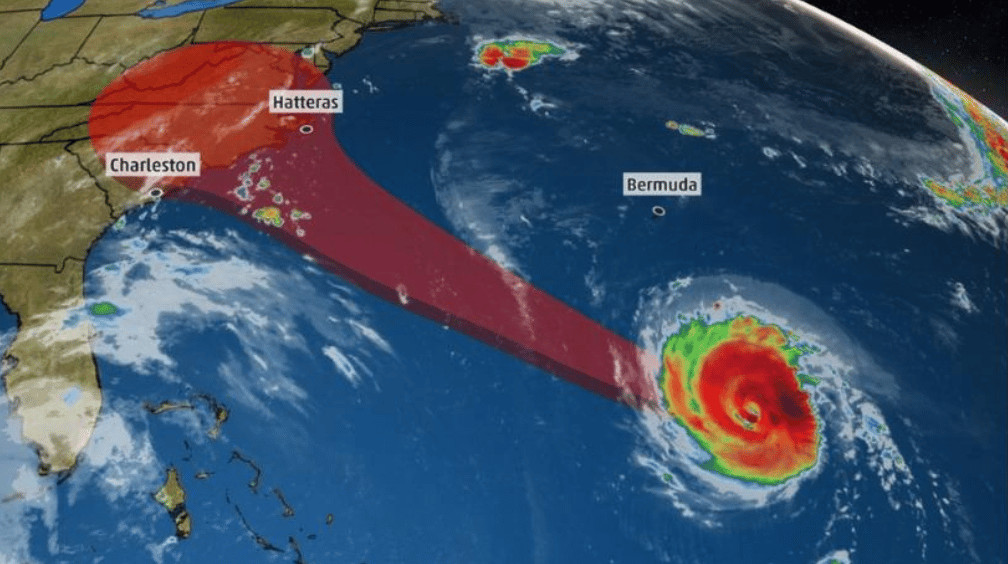
Hurricane Florence strengthens to Category 4 Evacuation Orders Begin in the Carolinas The National Hurricane Center is now saying that…
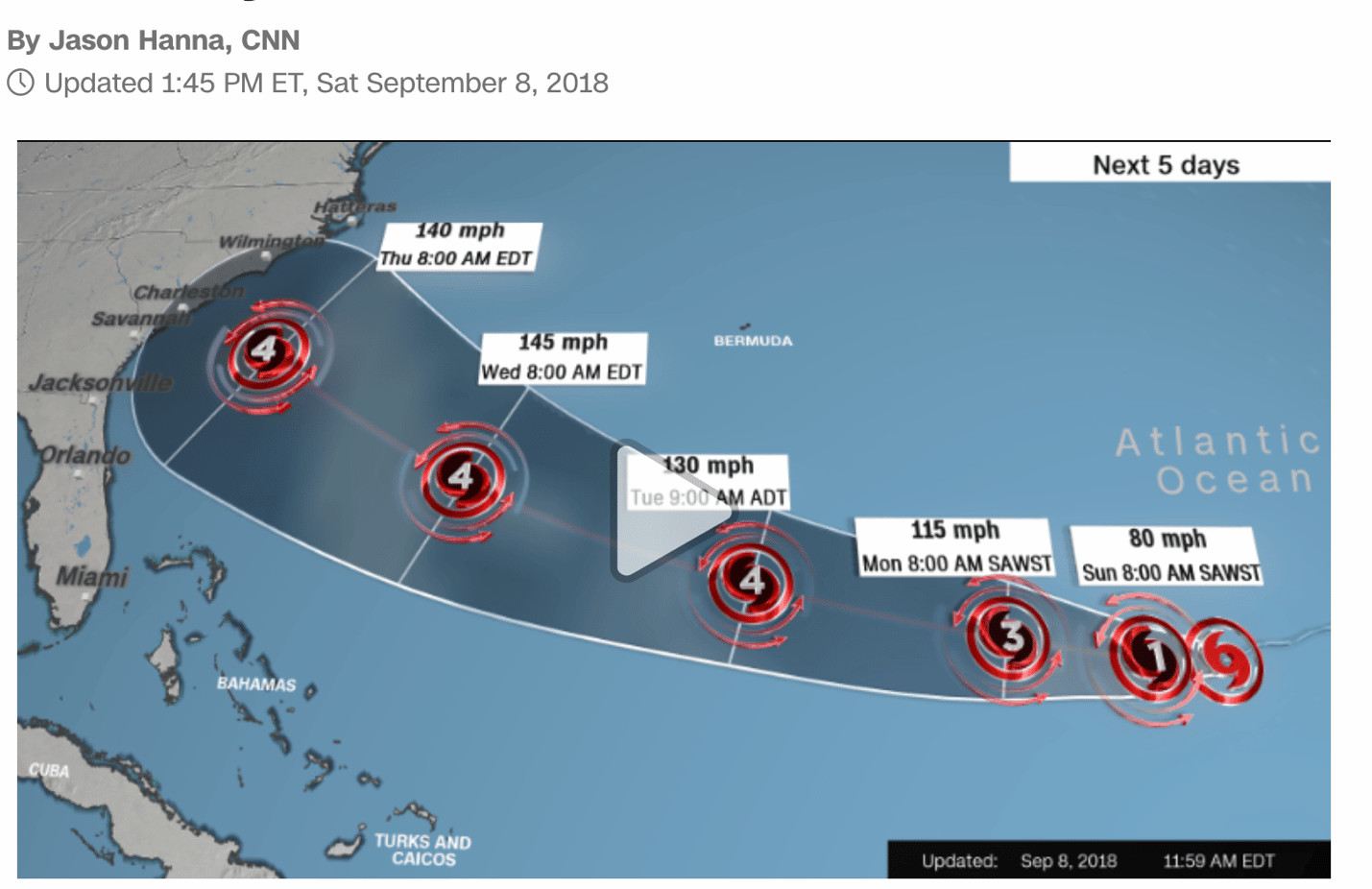
Florence is spinning up to be a Category 4 Hurricane. It’s predicted to make landfall between North Carolina and Georgia…
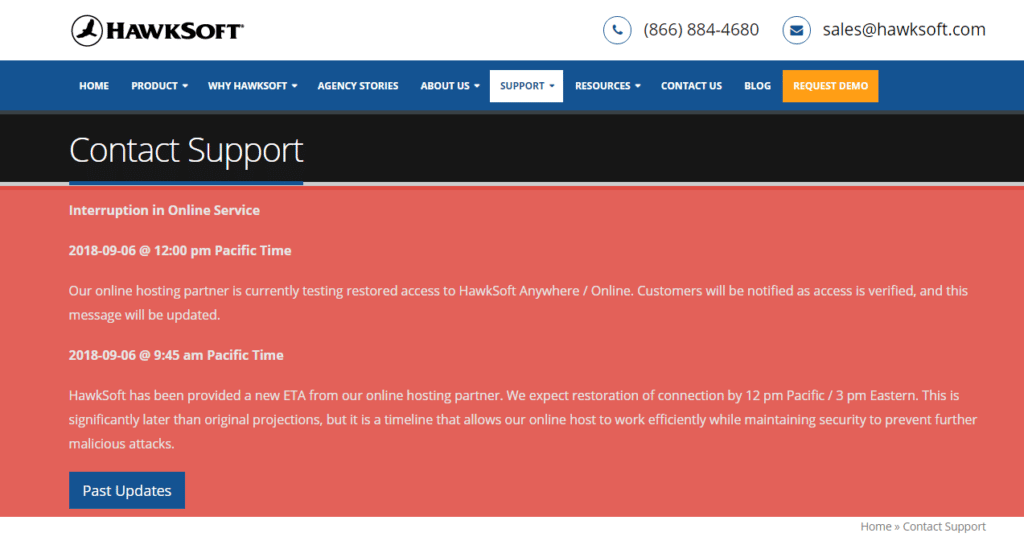
When companies fail at or are not prepared for a catastrophe, it’s often because they neglect to think that the…

What is PMKID? Pairwise Master Key Identifier (PMKID) is a type of roaming feature in a network. Recent improvements in…

Experts agree that the legal sector is not really on the cutting edge when it comes to adopting the latest…

Microsoft Teams is a great way to schedule meetings, especially if the participants don’t all work in the same geographic…